Data migration planning checklist
There’s no substitute for a structured plan to reduce the risk of problems occurring during a data migration. Our bespoke methodology for data movement projects includes a high level process checklist, followed by a checklist of tactical requirements. We find that working through these two sets of items ensures that data migration projects are delivered on time and to budget.
Process checklist
Our full data migration process covers a large scale data migration, from planning to legacy system retirement. Alternatively, we select the appropriate components for a specific project.
Depending on the client’s requirements, our consultants ensure that the following aspects are thoroughly planned:
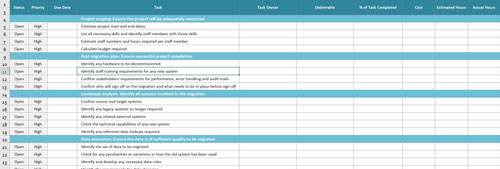
- Project scoping. A high level review to ensure that the project will be sufficiently resourced. Typically, data movement projects are under-resourced, and this stage tells the business upfront how much time, money and personnel will be required.
- Landscape analysis. Discovering all the systems that will be involved is critical. The assessment often finds that this is far more extensive than just the core source/target system.
- Data assurance. Making sure the data is of sufficient quality to move is crucial. This step can involve developing data rules, but also asks questions such as where and how data quality issues are fixed and ensuring any relevant regulations are satisfied.
- Core migration. This is the implementation of the data movement solution, but the plan should always include testing as well as deployment.
- Legacy decommissioning. If we’re moving data from a system that is currently in use, but is to be turned off, we plan how that business can continue when that system is decommissioned. For large migrations, this can include decommissioning buildings, hardware and staff. For smaller project movements, ensuring that users are able to continue to do their jobs – training, checking the technical capabilities of the new system and so on – may be all that’s required.

Tactical checklist
A typical tactical checklist includes all the specific areas our consultants need to review to make a data migration project a success:
- Understanding the source system. What subset of data do we need to move? Are there any peculiarities or variations in how the system has been used?
- Accessing the source and target systems. We need to develop programmatic access, for example using an SDK to access the source data and a Java access method for the target. Our consultants also need to find a way to access the metadata (descriptions of the data types) and the data itself. We also need physical access to representative systems to investigate and develop the solution iteratively.
- Interpreting the source data. For instance, what UoM or CRS is used?
- Identifying domain experts. We will sometimes need subject matter experts for both the source and target systems. Our consultants work with them to develop the mapping specification.
- Data quality. Are there requirements for cleansing data, running rules against the source data or against the data once loaded into the target? What is the workflow for improving data quality to satisfy data governance regulations?
- External systems. Are there other systems involved? For instance, do the client’s staff extract data into Excel and use that for their day-to-day work, or do they reference data systems? Sometimes reference data lookups need to be created, to enable standardisation.
- Testing. Our consultants work with relevant people in the client’s team to develop use cases for unit/integration testing. How will user acceptance testing be performed?
- Deployment. Is this a continuous process or a one-off? Who will run the data movement, and how? Does it plug into a workflow engine, for example? Are there restrictions on when it can be run?
- Performance. What are the client’s requirements for performance, error handling and audit trails?
- Contacts. Our consultants identify stakeholders and sponsors within the business to answer questions, ensure necessary support and provide access to resources.
- Access issues. Our requirements may include security clearance, the ability to install software or to add our own machines to the relevant networks.
- A definition of successful completion. Who needs to sign off on the project? What needs to be in place for the sign off to occur?
Access the spreadsheet version here
To get a free copy of the checklist as a fully customisable Excel spreadsheet, please complete the form below.
We will email you with a link to the spreadsheet and you will be added to our no-spam email newsletter list. Your contact details will never be shared with anyone else, except that your data will be processed by EmailOctopus in a third country, and you can unsubscribe at any time in one click. Click here to read our privacy policy.

Related posts you may like.
This website uses cookies to make our site work and to help us improve it. Cookies will be set on your device to remember your preferences. You can opt-out by clicking the Reject button.AcceptReject Read More
Privacy & Cookies Policy
Privacy Overview
This website uses cookies to improve your experience while you navigate through the website. Out of these, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. We also use third-party cookies that help us analyze and understand how you use this website. These cookies will be stored in your browser only with your consent. You also have the option to opt-out of these cookies. But opting out of some of these cookies may affect your browsing experience.
Always Enabled
Necessary cookies are absolutely essential for the website to function properly. This category only includes cookies that ensures basic functionalities and security features of the website. These cookies do not store any personal information.
Non-necessary
Any cookies that may not be particularly necessary for the website to function and is used specifically to collect user personal data via analytics, ads, other embedded contents are termed as non-necessary cookies. It is mandatory to procure user consent prior to running these cookies on your website.




